This CVE resulted from a product study project I conducted with the one and only: Gad Abuazira ![]()
How it all started?
My Dell computer often has a low battery issue. I called Dell assistance to find out what was going on because I had a product warranty.
I was instructed to download the aforementioned item: https://www.dell.com/support/incidents-online/he-il/remoteassist.
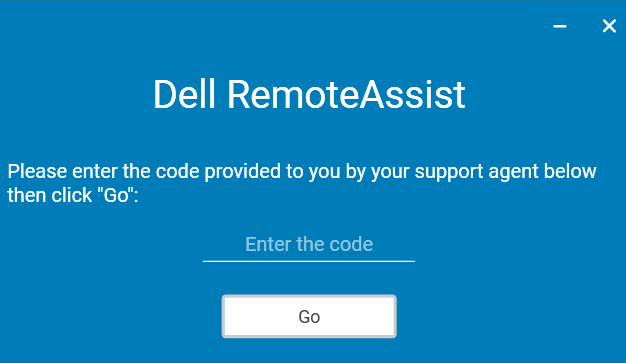
figure 1.0
The ‘code’ was mailed to me, and then we began a session where the supporter could manage my PC:
figure 1.1
I divided my computer into two screens so that the supporter could work on one screen while I launched WireShark on the other ![]()
The communication between my PC and their server was then visible to me.
Scanning for fun
To facilitate the scanning process, I used netstat to determine which IP address and port DellRemoteAssist.exe had open on my PC:
figure 1.2
TCP 192.168.68.105:54264 75.2.88.11:443 ESTABLISHED 1216
TCP 192.168.68.105:54265 75.2.88.11:443 ESTABLISHED 1216
I could now search more precisely on WireShark:
figure 1.3
Rate Limit bypass discovery
Figure 1.0 shows that there is a “code” that we insert and connect to the supporter. The request looks like this when burp intercepts it:
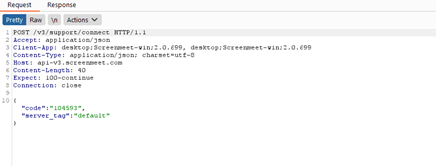
figure 2.0
Two fields are included in the request:
- The ‘code’ that the Dell support assistant provided to the user.
- ‘server_tag’ with the default setting.
There is no limit on your request if you sent it to Intruder and brute-forced the “code” field.
There are many 200 status codes scattered throughout the requests that identify other users’ support sessions:
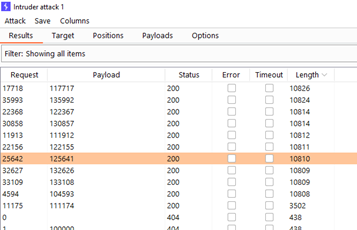
figure 2.1
The response includes private user and supporter data:
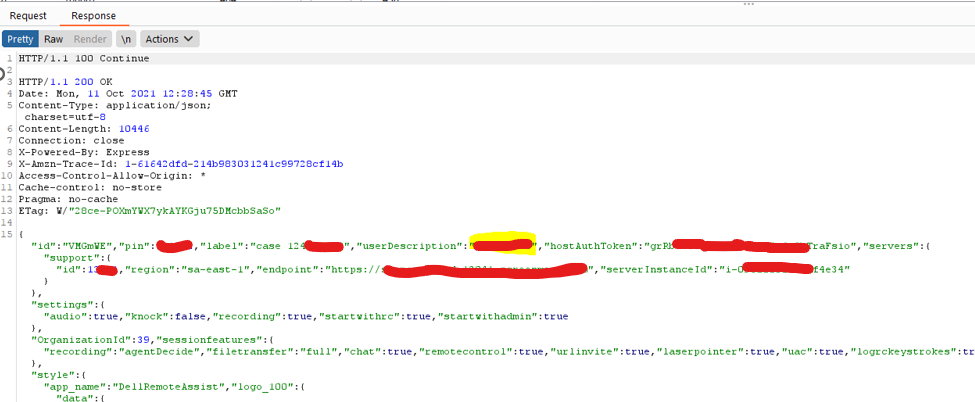
figure 2.2
We moved to the supporter-user session after entering the other user’s code:
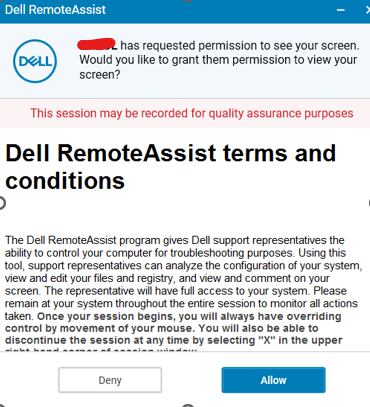
figure 2.3
The end ![]()